联系方式
more本类最新英语论文
- 2017-11-30美国原住民对经济的影响 im..
- 2017-08-28美国留学生社科作业:how m..
- 2017-08-24耐克公司的二次源整合secon..
- 2017-07-14美国early childhood educa..
- 2017-07-11美国留学生作业:关于自我的..
- 2017-06-21美国作业:调查的安全通信云..
- 2017-06-05美国留学生作业:南亚女性主..
- 2017-04-05志愿者管理已成为一个重要问..
- 2017-02-08人权宣言;分析 declaratio..
- 2017-01-11领导者应该影响和激励追随者..
more热门文章
- 2011-07-05代写美国留学生市场营销作业..
- 2017-04-05志愿者管理已成为一个重要问..
- 2011-07-04narrative essay-美国留学生..
- 2014-05-25《看不见的人》主题表现手法..
- 2014-06-13美国独立审计论文范文
- 2014-10-23国际维和行动的留学生论文怎..
- 2014-10-14留学生课程作业:美国全球性..
- 2016-04-23互联网络及移动通信
- 2017-06-21美国作业:调查的安全通信云..
- 2014-08-05文化差异对汉语典故英译的影..
more留学论文写作指导
- 2024-03-31卡森•麦卡勒斯小说中..
- 2024-03-28美国黑人女性心理创伤思考—..
- 2024-03-27乔治·艾略特《织工马南》中..
- 2024-03-21超越凝视:论《看不见的人》..
- 2024-03-19《哈克贝利•费恩历险..
- 2024-03-13心灵救赎之旅——从凯利的三..
- 2024-02-22文学地理学视角下的《印度之..
- 2023-05-03英、汉名词短语之形容词修饰..
- 2023-02-07目的论视域下5g—the futur..
- 2022-07-04二语英语和三语日语学习者的..
美国作业:调查的安全通信云第三方认证
论文作者:www.51lunwen.org论文属性:作业 Assignment登出时间:2017-06-21编辑:cinq点击率:9231
论文字数:2000论文编号:org201706211201205698语种:英语 English地区:美国价格:免费论文
摘要:本文是美国留学生作业范文,主要内容是介绍云计算的基本定义和内容,以及云计算作为一种信息技术,如何通过第三方认证。
Abstract 摘要 — Cloud computing is an information technology where user can remotely store their outsourced data so as enjoy on demand high quality application and services from configurable resources. Using information data exchange, users can be worried from the load of local data storage and protection. Thus, allowing freely available auditability for cloud data storage is more importance so that user gives change to check data integrity through external audit party. In the direction of securely establish efficient third party auditor (TPA), which has next two primary requirements to be met: 1) TPA should able to audit outsourced data without demanding local copy of user outsourced data ; 2) TPA process should not bring in new threats towards user data privacy. To achieve these goals this system will provide a solution that uses Kerberos as a Third Party Auditor/ Authenticator, RSA algorithm for secure communication, MD5 algorithm is used to verify data integrity, Data centers is used for storing of data on cloud in effective manner with secured environment and provides Multilevel Security to Database .
I. Introduction 简介
CLOUD computing is self-service demanding, ever-present network access, and location independent resource brings together, rapid resource flexibility. As cloud computing makes more attractive yet, it creates new and challenging security threats just before user outsourced data [1].
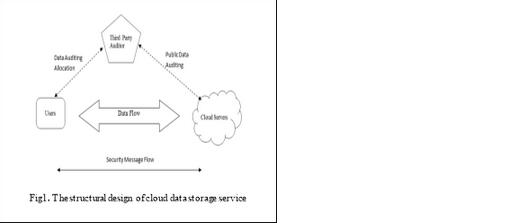
Consider a cloud data storage service having three different entities, as shown in Fig.1: cloud user, in which huge data files to be saved in the cloud; third-party auditor, which has information and facility that cloud users do not have and which have faith to access the cloud storage service consistency on behalf of the user request ; cloud server, which is handled by the cloud service provider and provide data storage service, large amount of storage space and computation resources [1],[4].
To completely guarantee on the data integrity and save the cloud user’s working out resources as well as online load, it is more significant to allow public auditing service for cloud data storage, As a result users may have option to an independent third-party auditor (TPA) who is expertise and having the capabilities that user do not, which periodically check the integrity of all data stored in cloud on behalf of user’s and which ensure their storage correctness in cloud [1], [3].
The rest of paper is organised as follows: section 2 introduce literature review in which it provide different technique to solve problem related cloud storage security but they have some drawback which can overcame by proposed system which is explain in section 3 that means it provide efficient solution against problem definition and literature review through various cryptography algorithms and third party auditor. Finally section 4 gives the concluding remark of whole paper and on the literature review.
II. LITERATURE SURVEY 文献调查
A. The Provable Dat本论文由英语论文网提供整理,提供论文代写,英语论文代写,代写论文,代写英语论文,代写留学生论文,代写英文论文,留学生论文代写相关核心关键词搜索。

 英国
英国 澳大利亚
澳大利亚 美国
美国 加拿大
加拿大 新西兰
新西兰 新加坡
新加坡 香港
香港 日本
日本 韩国
韩国 法国
法国 德国
德国 爱尔兰
爱尔兰 瑞士
瑞士 荷兰
荷兰 俄罗斯
俄罗斯 西班牙
西班牙 马来西亚
马来西亚 南非
南非